Spam-pm: Investigating the Spam Invasion of npm
A deep dive into the growing issue of spam flooding the npm public registry.
Greetings, fellow developers! You might have noticed some unusual activity on the npm registry lately, and indeed, you’re not alone. npm has been a target of a massive (and ongoing) spam attack. This post will guide you through these turbulent waters, so let’s fasten our belts and plunge in! 🌊
# When the spam hits 🦹♂️
Recently, the npm ecosystem has victim of a series of spam-related incidents. This spam tsunami has been building up since the beginning of 2023, and it doesn’t seem to be slowing down.
The user TotalCoder flagged this issue in a tweet on Feb 21, 2023:
So I've been noticing a spam attack on @npmjs. Tens of thousands of packages have been flooding the registry and occupying the front page. pic.twitter.com/T209xwOTAo
— Jesse Mitchell (@TotalCoder) February 21, 2023
The listen.dev team has been monitoring the situation closely and detected a first-of-its-kind spam surge on the npm public registry on March 29. The chaos continued over the weekend, with a whopping 500k packages published.
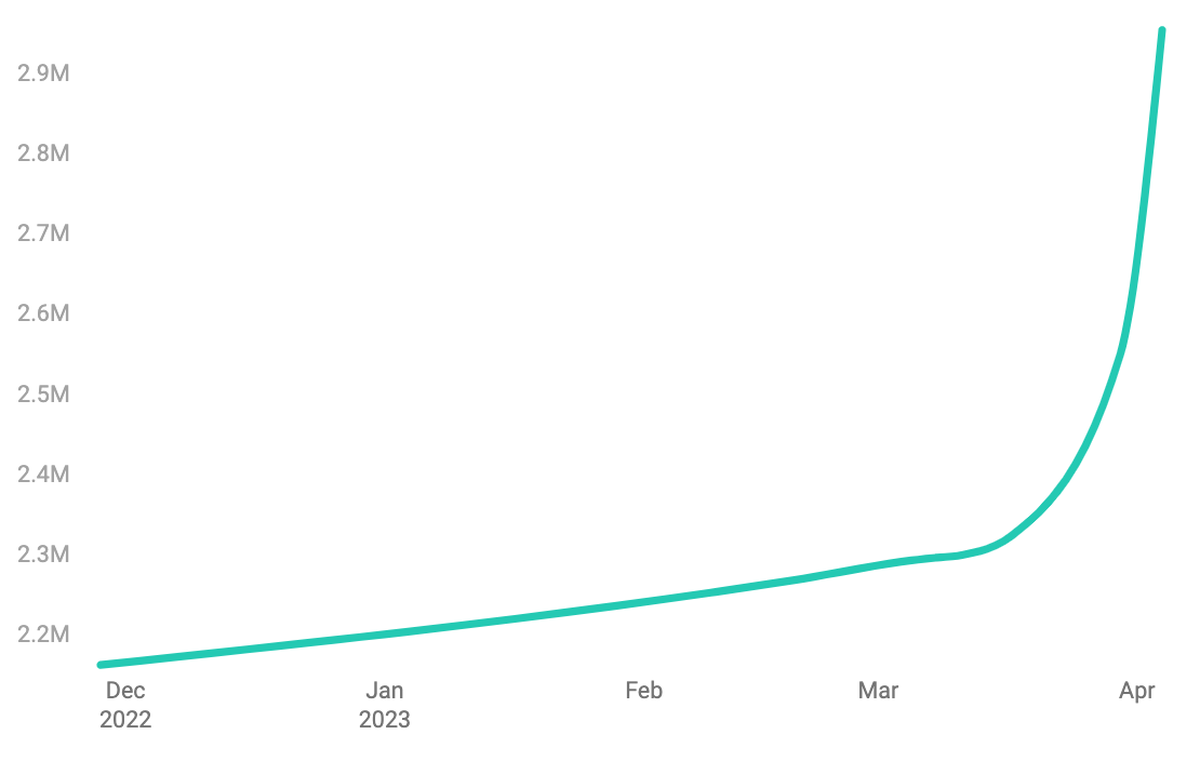
Extrapolating at current rate of 100k packages published per day (at the time of writing), the total number of packages on the npm registry would be 3,353,642 one week from now, and 5,953,642 in a month. That is more than double the current size of the npm index! 🤯
As of Apr 4, 2023 more than half of the newly published packages on npm are spam
# Spotting the Spam Package Epidemic 🕵️♀️
These digital delinquents have been spreading faster than a cute cat meme, targeting common themes like cryptocurrency, P2P trading, and get-rich-quick schemes. But we’ve cracked their code! Here’s a handy list of technical characteristics to help you spot these sneaky packages:
- Lack of Technical Content: Spam packages have promotional descriptions (typically containing links) with little or no code or technical information.
- Zero Dependencies and Dependents: Spam packages typically have no listed dependencies or dependents, indicating a lack of legitimate functionality.
- Unusual Package Names: Spam packages often have long, complex, or nonsensical names that do not reflect their purpose.
- Same or Similar Descriptions: Spam packages from the same user may have identical or very similar descriptions, indicating the use of templates and automation.
- High Volume of Published Packages: Users publishing spam packages may have an abnormally large number of packages published in a short time, indicating automated or mass publication techniques.
- Single-Version Packages: Spam packages often have only one version, suggesting a lack of maintenance or updates.
# A Closer Look at the Spam
The open-source npm ecosystem is inundated with nonsensical spam packages featuring phishing or Telegram links in README.md files. These packages primarily target topics such as cryptocurrency, P2P trading, financial strategies, and get-rich-quick schemes to exploit unwary users. The sheer scale of these campaigns suggests the utilization of automated scripts for generating and distributing these modules.
To better understand the nature of spam packages, let’s examine two examples. The first example is a package called binance-ne-prisylaet-kod-na-telefon-kmrojld, published by the user cikvoroooeiiei with the email npmwork1@gmail.com.
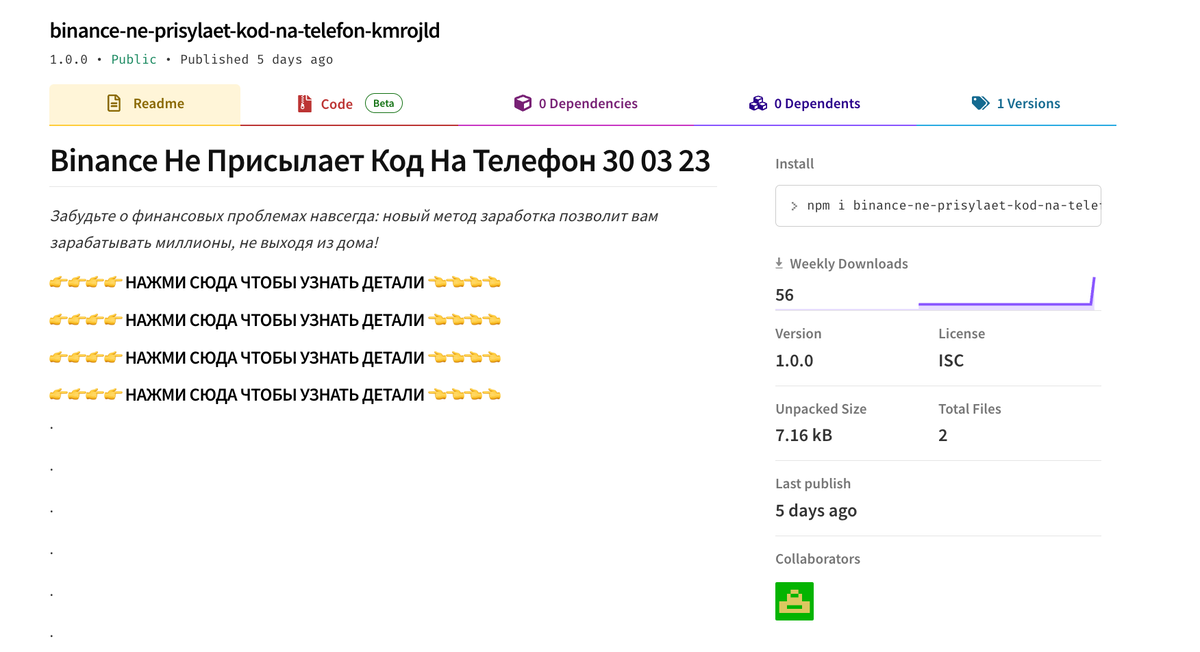
The second example is a package called 1xbet-zerkalo-1xbet-zerkalo-20233-akk-ru-ixkt, for which the maintainer are is listed as dsajkdhjasjhdhkdas. The email associated with the package is ftbwork30@gmail.com, and it has a description in Russian which translates to:
Forget about financial problems forever: a new method of earning will allow you to earn millions without leaving your home!
# Who’s Behind the Spamvasion? 👽
Meet the folks behind suspiciously high numbers of published packages, such as this “avid” maintainer cikvoroooeiiei from our earlier example, who boasts a whopping 47,433 package contributions on the registry. While the two packages in the example have distinct maintainers, a deeper investigation reveals that both packages actually originate from the same author, P2Pshnik! Interesting…
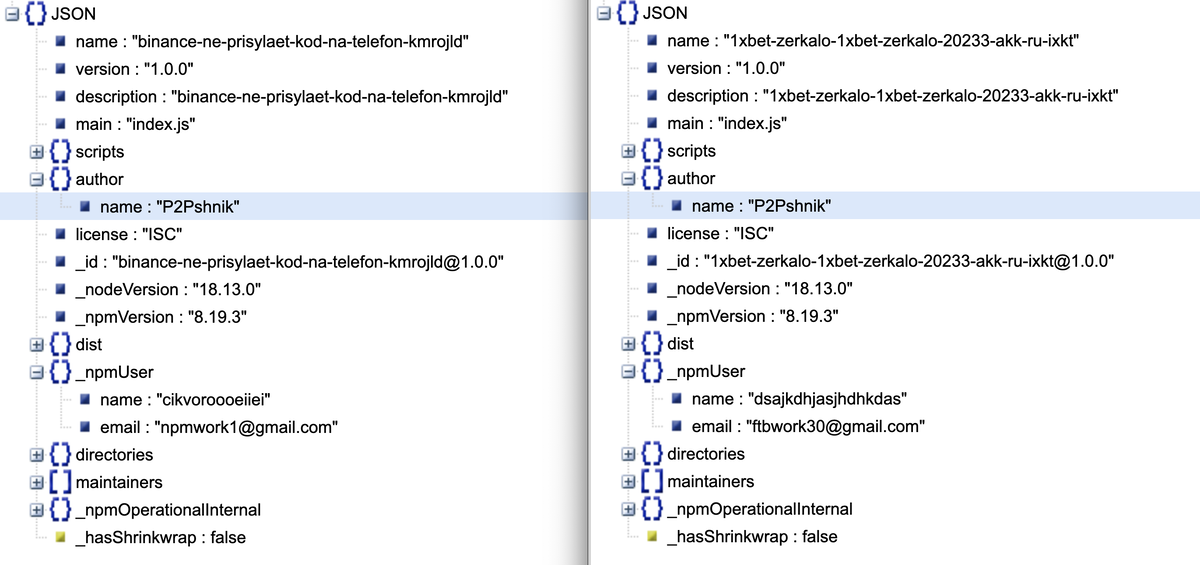
A similar trend was observed in some of the other examples we observed. The table below summarizes the characteristics of a few publishers we identified:
| npm User | Author | # of Packages | Key Words | |
|---|---|---|---|---|
| cikvoroooeiiei | P2Pshnik | 47,433 | npmwork1@gmail.com | zarabotok, p2p, skachat, crypto |
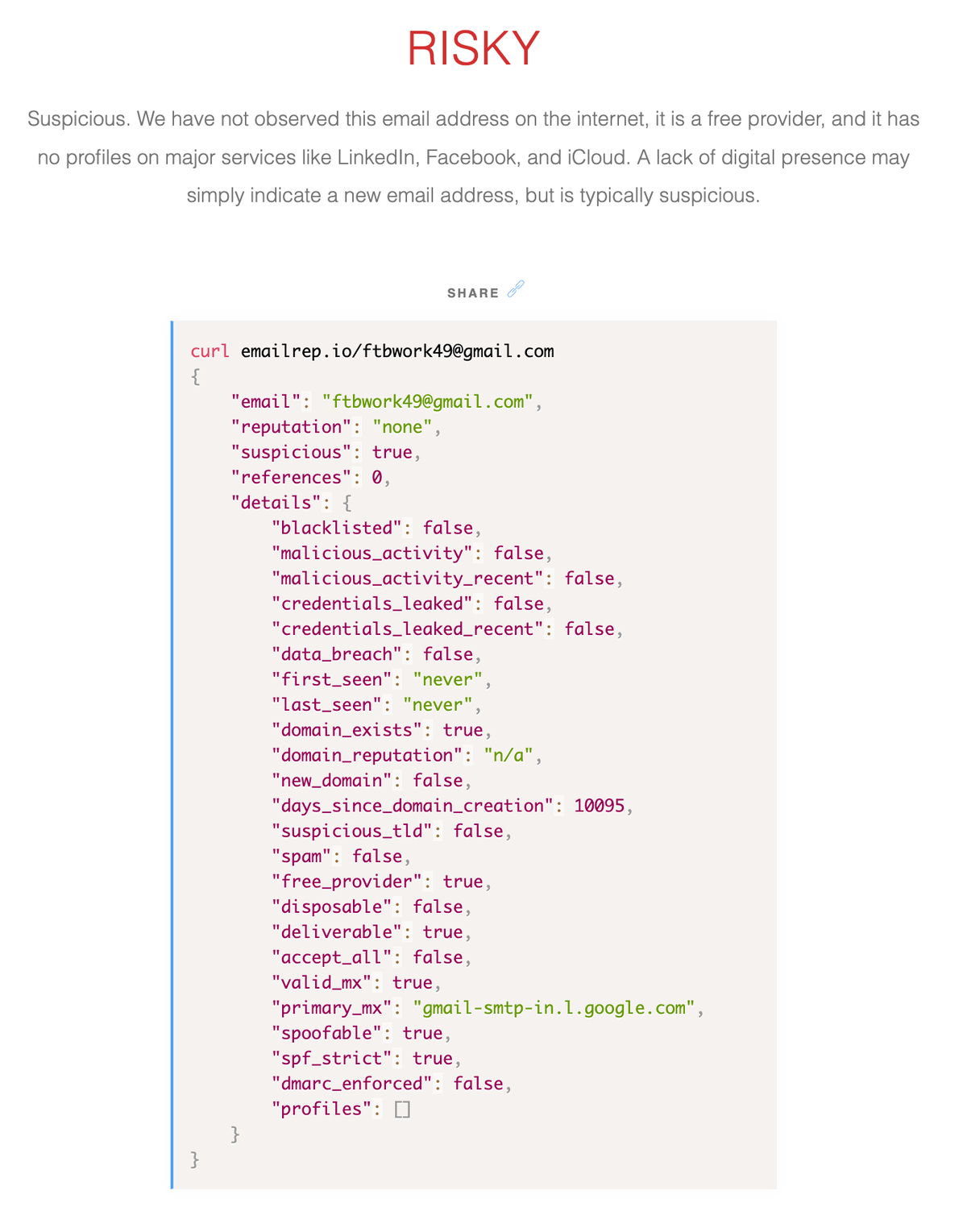
| jfeifieikkjdkejde334 | P2Pshnik | 43,142 | ftbwork49@gmail.com | zarabotok, p2p, skachat, crypto |
| vreopppproo23 | Viktor P2P | 36,462 | ftbwork50@gmail.com | gazproma, p2p |
| npmpublishq | P2Pshnik | 34,388 | npmwork2@gmail.com | zarabotok, skachat, p2p, crypto |
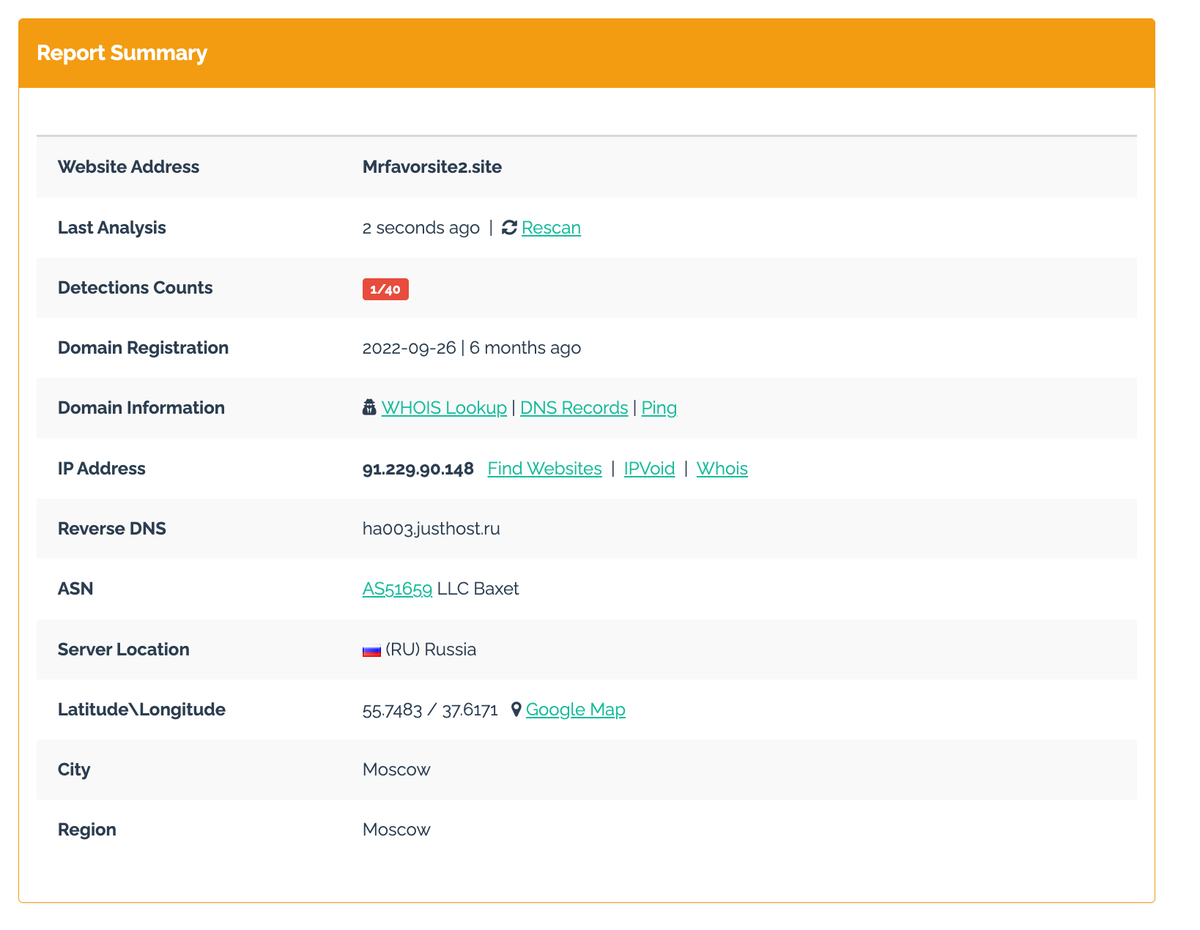
Upon looking up the domain and email reputation for the user jfeifieikkjdkejde334:
# Interesting findings
- The package names are a mix of popular cryptocurrency exchange names (such as Binance), gambling sites, and vague financial terms, and can be found in Russian, Latin, English, and other languages. For example, The word “zarabotok” (translating to “earnings” in English), was found in 31,144 packages.
- The majority of these spam packages stem from one Telegram channel focusing on delicate subjects like the conflict in Ukraine and investment choices made by Gazprom (a Russian multinational energy company). Clicking the Telegram link leads you to the following page:

- Certain packages utilize URL shorteners and trustworthy links to circumvent reputation concerns and might also participate in phishing schemes. Additionally, the entities behind these packages benefit from referral bonuses by guiding the audience to retail websites using referral IDs in the posted URLs.
# What This Means for Us (and npm)
So why the spam surge? As we dig deeper into this, a few potential motives come to mind:
- SEO manipulation: Including links to malicious websites in a large number packages to manipulate search engine rankings (SEO) rankings (Read: leveraging npm’s domain authority to promote spam)
- Hijacking resources: Spamming the registry with packages could lead to a DoS situation, disrupting legitimate users and normal operations.
- Phishing and scams: Deceiving users into visiting linked websites, leading to phishing attacks or scams, potentially exploiting users’ trust in the registry.
- Reputation damage: Flooding the registry with low-quality and malicious packages to create distrust among developers and consumers of the ecosystem.
Additionally, more sinister motivations behind this kind of a spam attack could include:
- Testing security measures: this could be a PoC assessing the registry’s defenses and uncovering potential vulnerabilities that could be exploited in future attacks.
- Overloading the npm reporting backlog: some of the packages have been sitting in the registry for over a week (at the time of writing), which implies that the npm security team is severly backlogged. The longer malicious packages remain accessible, the higher the risk of compromise as downloads increase.
- Duping analysis tools: by overwhelming security teams and analysis tools, particularly those relying on static analysis, with a massive influx of spam, malicious actors can sow confusion and divert attention from a more significant supply chain attack. With millions of spammy packages in circulation, tracking genuine malicious code becomes increasingly difficult, allowing the real target to slip under the radar.
As we continue to unravel the intriguing and ongoing developments surrounding the spam surge in the npm ecosystem, stay tuned for updates on this topic. In the meantime, it’s crucial to remember that with great npm power comes great responsibility. Remain vigilant, maintain clean code, and manage your dependencies proactively to stay safe from emerging threats (check out what we’re building at listen.dev).
Happy coding, and may the force (of clean npm packages) be with you! 🚀
