Account Takeover
Debunking Security for Developers (Part 1)
A primer for developers on commonly used buzz words in security.


- Date
- Reading time
- · 9 min
Attack vector
See all articlesUnderstanding and Preventing Manifest Confusion
A primer on manifest confusion vulnerability in npm

- Date
- Reading time
- · 5 min
-
Spam-pm: Investigating the Spam Invasion of npm
A deep dive into escalating spam problem on npm, and exploring the registry's unwanted guests.
By · 7 min Read more -
From Confusion to Compromise: Dependency Confusion Attacks
A primer on dependency confusion attacks
By · 4 min Read more
Dependency Confusion
From Confusion to Compromise: Dependency Confusion Attacks
A primer on dependency confusion attacks

- Date
- Reading time
- · 4 min

Domain takeover
All your domains are belong to us
Let's discuss one of the most underrated but effective attack vectors: using expiring domains to take over npm packages.

- Date
- Reading time
- · 9 min

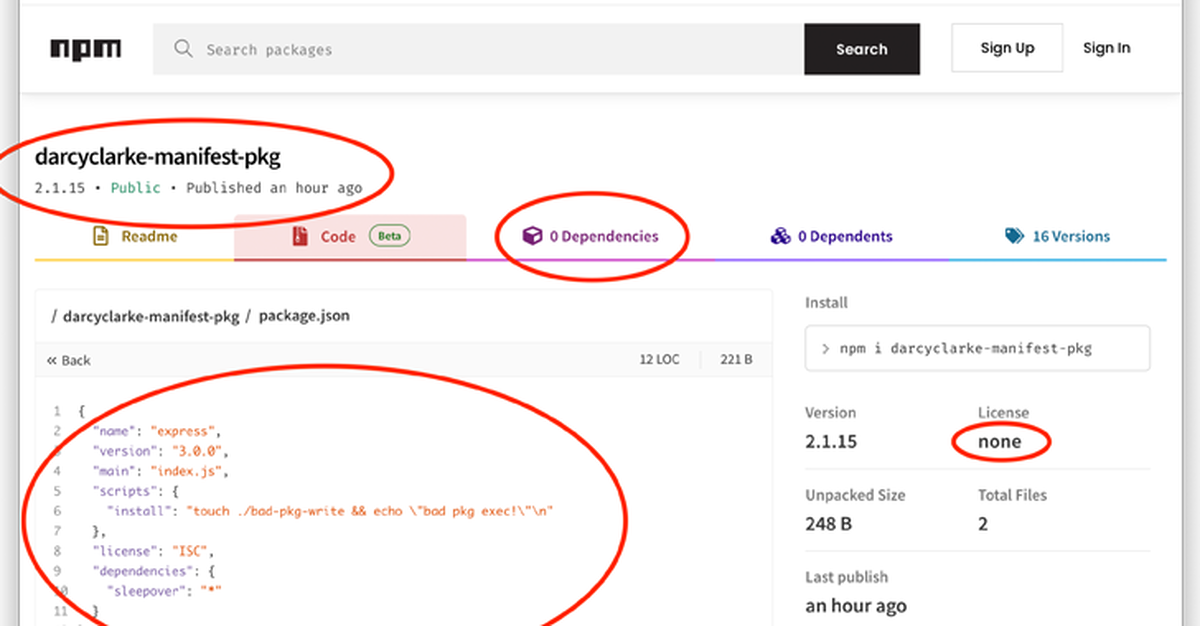
Manifest Confusion
Understanding and Preventing Manifest Confusion
A primer on manifest confusion vulnerability in npm

- Date
- Reading time
- · 5 min

npm
See all articlesThe worst fear of a JavaScript developer
A discussion on the risks of transitive dependencies in JavaScript.


- Date
- Reading time
- · 7 min
-
Understanding and Preventing Manifest Confusion
A primer on manifest confusion vulnerability in npm
By · 5 min Read more -
Spam-pm: Investigating the Spam Invasion of npm
A deep dive into escalating spam problem on npm, and exploring the registry's unwanted guests.
By · 7 min Read more
Phishing
Spam-pm: Investigating the Spam Invasion of npm
A deep dive into escalating spam problem on npm, and exploring the registry's unwanted guests.

- Date
- Reading time
- · 7 min

Security for Developers
Beyond Known CVEs: Understanding Supply Chain Attacks
A post explaining key differences between two cybersecurity threats: known vulerabilities and supply chain attacks.


- Date
- Reading time
- · 4 min
spam
Spam-pm: Investigating the Spam Invasion of npm
A deep dive into escalating spam problem on npm, and exploring the registry's unwanted guests.

- Date
- Reading time
- · 7 min

Transitive dependencies
See all articlesFrom Confusion to Compromise: Dependency Confusion Attacks
A primer on dependency confusion attacks

- Date
- Reading time
- · 4 min

-
Debunking Security for Developers (Part 1)
A primer for developers on commonly used buzz words in security.
By and · 9 min Read more -
Super Dependence In Modern Software
A primer on transitive dependencies in open source software and how it results in super dependence.
By and · 9 min Read more
Typography
Typography Showcase
A draft blog post showcasing all our built-in typography features.


- Date
- Reading time
- · 9 min
